Cloud Hosted Services: Some security considerations
A multi-cloud approach enables organizations to move application services to various public cloud providers depending on the desired service level and price...
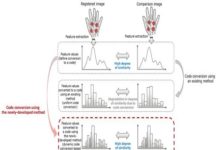
Encryption Technology for Biometric in Open Environments
Fujitsu Laboratories Ltd. has developed a technology that can compare biometric information while it is still encrypted, with the same accuracy and...
Cellular panic button reveals an NB-IoT future for personal safety alarms
The Nordic nRF9160-based Montr Emergency Button reaches places no other wireless signal can go such as deep basements commonly found below, for...
Thales & Tata Communications to develop Global IoT security solution
Thales and Tata Communications are working together to develop a secure global IoT connectivity solution. Tata Communications MOVE mobility and IoT platform...
Development of secure automotive systems with embedded monitoring capabilities
UltraSoC has joined AESIN (the Automotive Electronics Systems Innovation Network) to further its development of secure automotive systems with embedded monitoring capabilities. Such technology helps...
User-Programmable Scrambler IC to Protect Audio Systems Against Security Breaches
Recognising the growing need to protect communication systems from the threat of being compromised by unauthorised parties, CML Microcircuits has introduced the CMX7158. Based...
Sepio Systems Partners with Johnson Controls & Expands Advisory Board to Help U.S. Companies...
Sepio Systems, which is disrupting the cyber-security industry by uncovering hidden hardware attacks, is gaining momentum in the U.S. after adding an important new customer...
Challenges emerging in Securing Modern Applications
Securing modern day applications is becoming more and more difficult. Whether they are web or mobile, custom developed or SaaS-based applications are now scattered...
Major Bot Threats: CISOs recognise your Enemy
According to a study by the Ponemon Institute in December 2018, bots comprised over 52% of all Internet traffic. While ‘good’ bots discreetly index...
Importance of Security for a Business
Are you a business owner? If yes, you will be aware of the challenges to manage various aspects of your business. Right...