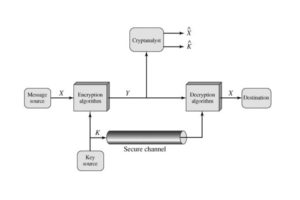
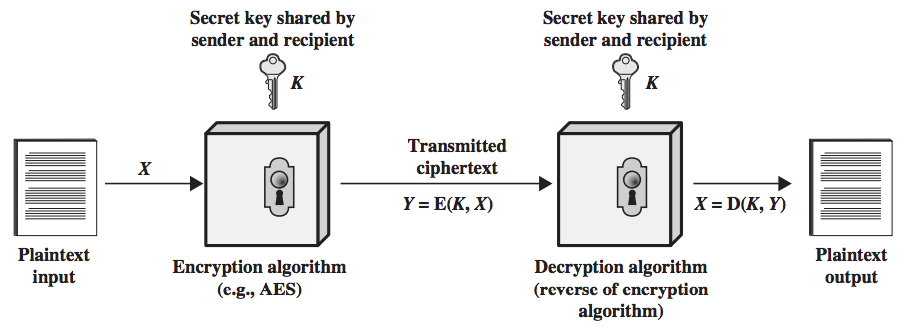
Symmetric encryption is also referred to as conventional encryption or single-key encryption. It was the only type of encryption in use prior to the development of public-key encryption. It remains by far the most widely used of the two types of encryption.
A symmetric encryption scheme has five ingredients:
- Plain text: This is the Original intelligible message or data that is fed in to the algorithm as input.
- Encryption Algorithm: The encryption algorithm performs various substitutions and transformation on the plain text to convert it into ciphertext.
- Secret Key: The secret key is also input to the encryption algorithm. The key is a value independent of the plain text. The algorithm will produce a different output depending on the specific key being used at the time. The exact substitutions and transformations performed by the algorithm depend on the key.
- Ciphertext: This is the scrambled message produced as output. It depends on the plain text and the secret key. For a given message, two different keys will produce different ciphertexts. The ciphertext is an apparently random stream of data and, as it stands, is unintelligible.
- Decryption Algorithm: This is essentially the encryption algorithm run in reverse. It takes the ciphertext and the secret key as the input and produces the original plain text.
There are two requirements for secure use of conventional encryption-
- We need a strong encryption algorithm. At a minimum, we would like the algorithm to be such that an opponent who known the algorithm and has access to one or more ciphertext would be unable to decipher the ciphertext or figure out the key. Usually, this requirement is stated in a stronger form. The opponent should be unable to decrypt ciphertext or discover the key even if he or she is in possession of a number of ciphertext together with the plain text that produce each ciphertext
- Sender and Receiver must have obtained copies of the secret key in a secure fashion and must keep the key secure. If someone can discover the key and knows the algorithm, all information using this key is readable.


















