Cause that lead to birth of microsegmentation-
A reknown research shows that more than 30 percent of data center issues are caused by cyber attacks, and a 60 minute breakdown can cost business upwards of half a million dollars.Cyber threats today are coordinated attacks that often include months of reconnaissance, vulnerability exploits, and “sleeper” malware agents that can lie dormant until activated by remote control. Despite increasing types of protection at the edge of data center networks – including advanced firewalls, intrusion prevention systems, and network-based malware detection – attacks are succeeding in penetrating the perimeter, and breaches continue to occur.
Microsegmentation and its meaning
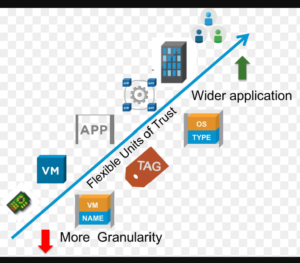
Micro-segmentation is a security technique that enables fine-grained security policies to be assigned to data center applications, down to the workload level. This approach enables security models to be deployed deep inside a data center, using a virtualized, software-only approach.
Microsegmentation and Data centre-
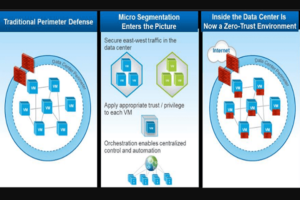
Microsegmentation divides the data center into smaller, more-protected zones. Instead of a single, hardened perimeter defense with free traffic flow inside the perimeter, a microsegmented data center has security services provisioned at the perimeter, between application tiers, and even between devices within tiers. The theory is that even if one device is compromised, the breach will be contained to a smaller fault domain.
As a security design, microsegmentation makes sense. However, if such a data center relies on traditional firewall rules and manually maintained access control lists, it will quickly become unmanageable. An organization cannot simply create a list of prohibited traffic between nodes; that list will grow exponentially as attack vectors, vulnerabilities, and servers multiply.
CISCO’S review
Cisco® Application Centric Infrastructure (ACI) provides true microsegmentation in an effective manner. Cisco ACI abstracts the network, devices, and services into a hierarchical, logical object model. In this model, administrators specify the services (firewalls, load balancers, etc.) that are applied, the kind of traffic they are applied to, and the traffic that is permitted. These services can be chained together and are presented to application developers as a single object with a simple input and output. Connection of application-tier objects and server objects creates an application network profile (ANP). When this ANP is applied to the network, the devices are told to configure themselves to support it. Tier objects can be groups of hundreds of servers, or just one; all are treated with the same policies in a single configuration step.
Advantages-
1. The only workable solution is a trusted declarative (white list) security model in which security services specify the traffic that is permitted and everything else is denied.
- This solution requires tight integration between application and network services, and that integration is lacking in most data center deployments.
3. Indeed, network analysis frequently demonstrates that applications are using unexpected traffic flows to deliver services, demonstrating the traditional disconnection between application, server, and network managers.
4. One major benefit of micro-segmentation is that it integrates security directly into a virtualized workload without requiring a hardware-based firewall. This means that security policies can be synchronized with a virtual network, virtual machine (VM), operating system (OS), or other virtual security target.
5. Security can be assigned down the level of a network interface, and the security policies can move with the VM or workload, in case of migration or reconfiguration of the network.
Microsegmentation provides internal control of traffic within the data center and can greatly enhance a data center’s security posture. Cisco ACI is the only solution available today that enables true microsegmentation with the performance, scalability, and visibility that modern applications demand.


















