
USB ports supply both data communications and charging power to portable and wearable devices, so it’s becoming more and more critical to protect ports against abuse.
Any aspiring evildoer can easily find a “USB killer” device that can destroy almost any USB port with a power surge attack that overwhelms the standard protection circuitry. The device looks much like a standard USB flash drive but contains a boost converter that feeds a bank of capacitors. When plugged in, the control circuit charges the capacitor bank via the USB power pin, discharges it into the data pins, and repeats the charge-discharge cycle, applying a series of -200V pulses until it’s unplugged.
Zap—game over, in under a second! Depending on the circuitry between the USB port and the rest of the design, such a power surge can destroy anything from the USB port itself to the whole machine. Plenty of YouTube videos exist that show the havoc wreaked on various pieces of equipment, including smartphones, laptops, tablets, and even smart TVs. In fact, some people derive positive enjoyment from this activity.
Fortunately, there are design techniques that reduce power surge risks to USB ports. USB Type-C™ offers a potential solution as well.

Design Techniques that Reduce Power Surge Risks to USB Ports
Many manufacturers offer USB protection devices, but their specifications are intended to protect against accidental events such as a finger touching an exposed USB pin—but not deliberate attempts at sabotage. The TPD4S214 from Texas Instruments (Figure 1), for example, is a single-chip device that offers low-capacitance transient voltage suppression (TVS) protection and electrostatic discharge
(ESD) protection for the D+ and D- data pins. The ESD protection meets the IEC 61000-4-2 Level 4 ESD protection standard and can withstand contact and air-gap ESD events up to ±15kV.
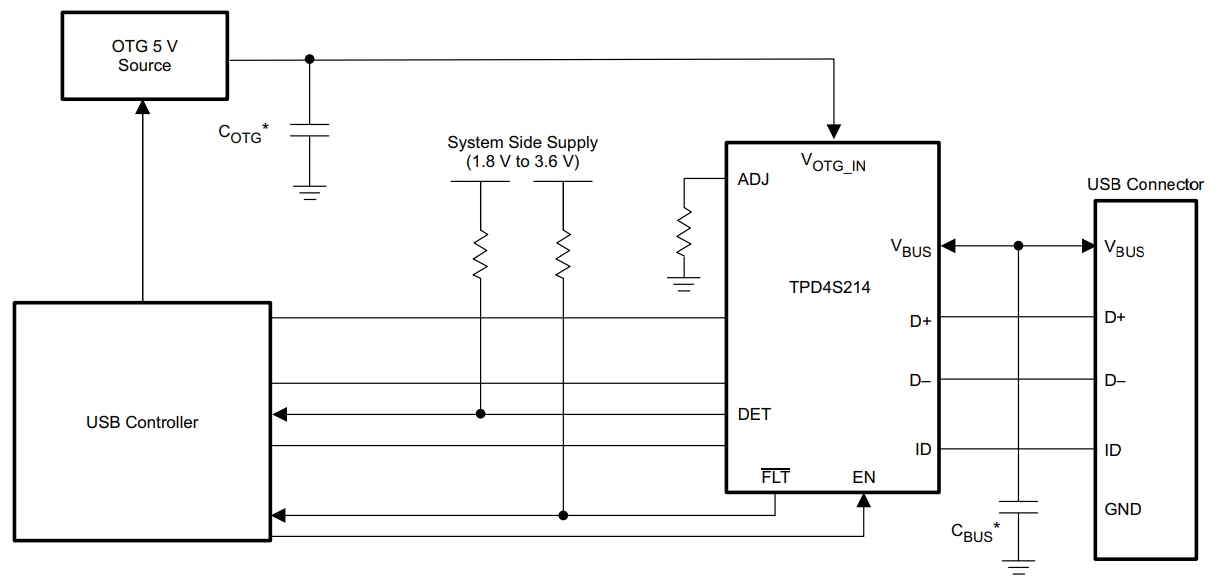
Figure 1: The TPD4S214 protects against expected electrical hazards, but not enemy action. (Source: Texas Instruments)
Could designers include more comprehensive protection? Of course, but in the price-competitive consumer market, it’s rarely worth adding expensive circuitry to guard against vanishingly-rare events that don’t involve the risk of injury or death. The tradeoffs are different in higher-dollar markets, such as the medical or industrial equipment markets, that use USB ports. Designers for these products have a bigger budget and more design options to protect the USB interface.
Optocouplers are relatively low-cost but aren’t suitable for the USB bus transceivers themselves: Not only must the USB interface be bidirectional, the delay and skew of the D+ and D- signals must also be carefully matched. Both requirements are difficult to achieve with optocouplers. Careful system partitioning can accommodate optical isolation further along the signal chain—e.g., by adding it to a serial peripheral interface (SPI). Such a solution may expose the interface to attack but protects expensive downstream processors and circuitry.
The gold standard for protection at the USB interface is galvanic isolation. Of course, given the price of gold, this option isn’t exactly low-cost; however, it’s a small price to pay if the alternative is risking the destruction of a $100,000 piece of equipment!
Analog Devices’ LTP2884 is designed just for a USB: It’s a USB 2.0-compatible, full-speed (12Mbps) transceiver combined with galvanic isolation that’s rated at 2,500VRMS. The LPT2884 can supply isolated peripherals with up to 2.5W (500mA at 5V) when used with an external supply or up to 1W (200mA at 5V) from an integrated DC/DC converter.
USB Type-C Offers a Possible Solution
What’s in the future? The latest revisions to the USB specifications, USB 3.0 and USB 3.1, increase the data speed to 5Gbps and 10Gbps respectively, making even isolation transformers impractical. Luckily, help is on the way. USB Type-C is the latest USB connector specification, and it’s beginning to replace the USB 2.0. Related to the USB Type-C is a USB Power Delivery (USB PD) specification that does away with USB 2.0’s simple 5V power delivery system. In its place, each pair of USB PD-capable devices negotiates a power transfer “contract” at the point of connection: The contract determines the direction of power transfers and selects the voltage and power level for use.
The USB 3.0 Promoter Group has released an authentication specification for USB Type-C that defines a cryptographic-based authentication protocol for USB Type-C chargers (power transmitters) and devices (power receivers). With the implementation of this protocol, host systems can confirm the authenticity of a USB device or USB charger immediately once a wired connection occurs—though before inappropriate power or data can transfer. Any authentication scheme can theoretically be defeated, of course, but requiring authentication before supplying any power should certainly make life a lot more difficult for would-be USB Type-C killers.
While You’re Waiting, Follow These Simple Precautions
Already-designed equipment, of course, can’t take advantage of these products. How, then, do you keep your USB 2.0-equipped tablet or laptop safe? For maximum protection, you can store your portable data in the cloud and physically block each USB port. At its simplest (and most permanent!), this might involve a USB cover and a dollop of superglue, but a more elegant solution is a USB-closing lock: This clicks into each USB port and can’t be removed without disassembling the case. Likewise, versions that can only be removed with a special security key are also available.
If you must keep your USB ports easily accessible, it’s time to fall back on a little old-school due diligence. Don’t insert flash drives given to you by strangers, or those you find on the ground or otherwise abandoned. Even if you trust the person giving you the drive, make sure they’ve used it before or purchased it from a legitimate, verified source such as Mouser. Finally, never leave your computer unattended where unauthorized persons can gain access.
Unfortunately, there’s no simple solution to the problem of USB-killing devices. But following a few simple precautions can ensure the safety of your laptop, tablet, or smartphone.
The blog was first published on Mouser Electronics.



















