STM32Trust TEE webinar
Is it possible to transform security on embedded systems from a burden to a blessing? It’s the question ST is trying to answer with STM32Trust, an initiative that focuses on all the software and hardware solutions we bring to improve the security of our devices as well as bring security expertise to non-experts. Information security, or InfoSec, can be a burden because it is so broad and complex. Hence, helping engineers means making ST tools more accessible. Indeed, taking advantage of all the features that a system offers is not always evident. Moreover, stringent certifications can increase costs and delay product launches. Developers thus need solutions to implement vital protections faster.
The latest initiative we announced in early 2023 was Secure Manager (more on that later). A few months later, we released the STM32H5, the first MCU to support the security initiative. And a few weeks ago, we published updates to STM32CubeProgrammer and STM32CubeMX that open up certain features provided by Secure Manager. To make Secure Manager even more accessible, we are excited to offer a webinar on September 7th, coinciding with the release of binaries that will allow developers to easily implement the new STM32Trust TEE. Hence, as the solution becomes available to all, the webinar will provide a step-by-step guide to get started.
How It Started and How It’s Going
As cloud connectivity is ever more present, it becomes imperative to safeguard credentials, encryption keys, and more to prevent attacks on server farms and other sensitive infrastructures. As our lives are increasingly digital, sensor data can seriously hurt a person’s privacy. Furthermore, governments are starting to mandate stricter cybersecurity rules. The European Union is working on its Cyber Resilience Act, while the United States passed the IoT Cybersecurity Improvement Act in 2020, to name two initiatives only. The challenge is that many are left wondering what safeguards they should put in place and the impact of the new laws on the future of their products.
STM32Trust is ST’s solution to this challenge, as it makes security more accessible and straightforward. It is a program that keeps growing as we release more software tools and products over time. The initiative also helps educate developers to ensure their knowledge is current. As a result, ST holds training, publishes papers, writes documentation, and works with partners to facilitate the obtention of certifications. In other words, exhaustively explaining all the aspects of STM32Trust in one blog post would be futile, which is why The ST Blog decided to focus on core solutions to help readers better visualize how they can implement security into their system.
What’s new: STM32 Trusted Execution Environment Secure Manager
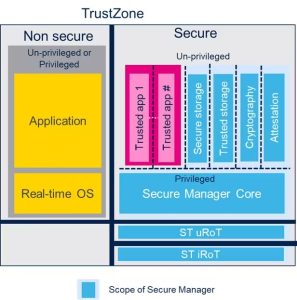
Secure Manager, announced recently, is the first Trusted Execution Environment solution by ST. Indeed, we offer binaries and, for the first time, handle the certification at the system level. As a result, customers targeting a SESIP & PSA Level 3 Certification can vastly hasten their qualification process. Available in June, it will only support the STM32H5 at launch but will be compatible with other STM32 MCUs over time. The Secure Manager will take the form of a downloadable software package containing binaries, libraries, code implementations, and documentation, among other things. There will also be configuration options in STM32CubeMX, ST’s initialization software, to guide developers in activating certain features like the STM32H5’s iRoT.
The most accessible security solution
Previously, ST only provided source code, which meant that developers had to adapt it and compile it, which would force them to certify the code again. Indeed, the qualification is only valid if the code remains unchanged. A binary guarantees just that. Additionally, Secure Manager provides a turnkey solution that automatically sets up the iRoT and features like secure storage, cryptography, and certificates, making the process much simpler. Companies only have to worry about the secure modules they design in-house and the final application that will run on the microcontroller.
Additionally, customers don’t have to worry about updating their system in case of an issue. Since we own the binaries and manage the stack, we can write and publish a patch. Even teams with significant expertise in the matter will appreciate the vastly simpler workflow. Indeed, unless a product has very specific needs, using ST’s binaries saves tremendous time and resources. We also provide a Secure Manager Access Kit (or SMAK) to help developers create applications that use services from the Secure Manager but run on the non-trusted part of the TrustZone environment.
The most comprehensive solution for advanced users
ST designed the new Secure Manager with flexibility in mind, thus allowing more seasoned developers to customize their solutions. For instance, it comes with the Secure Manager Development Kit (SMDK), which can help create complex and trusted applications. A team working on a fingerprint algorithm would thus use the SMDK to turn it into a secure and encrypted module living in a privileged area.
Moreover, thanks to the iRoT, programmers can store keys and certificates in the STM32H5, and thus register an embedded system to a cloud server without needing external keys. Therefore, Secure Manager on the STM32H5 frees companies from dealing with external hardware security modules, among other things. Cryptographic APIs also allow programmers to wrap and unwrap sensitive credentials using encryption keys without ever accessing them directly, thus protecting them from attacks.
STM32Trust and X-CUBE-SBSFU: Fashioning Secure Boot and Secure Firmware Update
Protecting Users From Start to Finish
Secure Boot is a program that runs at startup or reset to verify the integrity of the boot files by checking file size or signature to determine if anything changed. It thus protects the system from attacks that want to compromise the firmware during the boot sequence. Another type of protection is a secure firmware update. This method shields users from attacks that modify the existing system remotely. Indeed, when a server sends a partial or complete encrypted firmware image update, the embedded system transmits it via UART to the MCU, the system checks its authenticity, and then decrypts it before installing it.
A Much Easier Implementation
A package like X-CUBE-SBSFU allows developers to implement these features more easily. For instance, the code from X-CUBE-SBSFU that runs on our STM32L4 received a PSA Level 1 certification. Engineers can thus use it to receive the same accreditation much more quickly. Moreover, ST continues to make its source code available. As a result, developers can learn from our implementation and optimize their applications. For example, our libraries can generate 60 KB binaries approximately, which can be a bit large for some small embedded systems. However, optimization operations enable developers to trim the code and only use relevant functions to fit their MCU.
X-CUBE-SBSFU also serves other purposes as it helps teams take advantage of various STM32Trust tools. For instance, it uses our X-CUBE-CRYPTOLIB library to optimize cryptographic operations. ST recently overhauled the software package to offer a modular approach and certified code. Moreover, X-CUBE-CRYPTOLIB now segregates libraries according to the MCU to be more intuitive. X-CUBE-SBSFU also added support for STSAFE-A110, the tamper-resistant secure element, found on the STEVAL-STWINKT1B, that stores various keys and certificates.
STM32Trust and TF-M or TF-A: Creating Trusted Environments
Security Through Encryption, Verification, and Isolation
Both TF-M and TF-A are reference implementation of a Trusted Execution Environment (TEE). The former works on specific Cortex-M cores, while the latter is for Cortex-A devices. As the name implies, the point is to create trust by isolating and securing various aspects of the system. For instance, TF-M and TF-A leverage secure storage and cryptographic operations to secure the boot and update processes. Hence, they offer a way to guarantee the integrity of the Secure Boot mechanism and the firmware. They also sandbox runtimes to prevent an issue from affecting the whole system and enable services such as key storage as well as attestation and secure cryptography.
Building Trust on Cortex-M and Cortex-A Devices
Developers looking to use TF-M on a compatible STM32 microcontroller will find what they need in its software package. For instance, implementing TF-M on an STM32L5 starts with STM32CubeL5. The package has a reference implementation for significant features like secure boot, secure storage, secure isolation, and more. As a result, teams can create a mechanism similar to SFU but with standard isolation schemes.
We will also continue to improve our reference implementation over time to take advantage of more features. As for TF-A, since things are obviously different for an MPU, ST created a Wiki to guide engineers. It walks users through the major notions and software tools to rapidly implement a reference environment. Additionally, developers can also use OP-TEE, an Open Portable Trusted Execution Environment that serves as a companion solution for non-secure Linux kernels.
STM32Trust and SFI: Bringing Secure Firmware Install
Protecting Intellectual Property and Preventing Theft
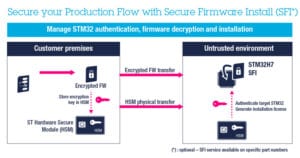
Secure Firmware Install is a mechanism that protects a customer’s binary from malicious activities. Very often, companies must rely on a third party to assemble their final product. The problem is that it can cause a great deal of anxiety and uncertainty. A rogue employee on the assembly line, or hackers, could steal the firmware, leading to catastrophic consequences. A secure firmware install protects against it by encrypting the firmware before shipping it to the OEM. Since decryption happens when the code is inside the MCU, the IP remains safe, and any stolen firmware is useless. Additionally, companies can even use this technique to track the number of firmware installations to monitor any product theft.
A Smart Card and STM32CubeProgrammer
SFI relies primarily on two tools. Developers encrypt their firmware with the Trusted Package Creator utility available within the STM32CubeProgrammer software and place their private keys and certificates in a secure hardware module that takes the form of a smart card.
Teams then ship the encrypted binary and smart card to the EMS. Assembly lines upload the firmware and keys over UART, I<sup>2</sup>C, USB, or JTAG via STM32CubeProgrammer. The smart card then validates everything by authenticating the MCU and getting its unique key. The card also sends a private key to decrypt the binary and generate an individual license for each product. The license enables the upload system to track the precise number of installs. Finally, ST recently released a new version of its smart card that allows companies to define their target device. Previously, the model of the MCU was setup in advance. With the new version, companies can load it to enjoy a more flexible system.
- Register for the STM32Trust TEE webinar
- Check out STM32Trust
- Discover X-CUBE-SBSFU
- Learn more about Secure Firmware Install (SFI)
- Pour over the new Secure Manager