The ransomware landscape in Q3 2025 has reached a critical inflection point. Despite multiple law enforcement takedowns earlier in the year, ransomware attacks remain at historically high levels. Check Point Research tracked 1,592 new victims across 85 active extortion groups, marking a 25% increase year-over-year.
While major brands like RansomHub and 8Base have vanished, new and smaller threat actors have rapidly filled the void, fragmenting the ransomware-as-a-service (RaaS) market more than ever before.
Record Fragmentation: 85 Active Extortion Groups
The number of active ransomware groups surged to a record high of 85, with 14 new groups emerging in Q3 alone. This represents the most decentralized ransomware ecosystem on record.
- The top 10 groups now account for just 56% of all victims (down from 71% in Q1 2025).
- 47 groups posted fewer than ten victims, signalling an influx of small, agile affiliates launching independent attacks.
This fragmentation means greater unpredictability for defenders. Small, transient groups lack reputation-driven incentives to deliver decryptors after payment, reducing victims’ chances of data recovery and further eroding trust in negotiation outcomes.
LockBit 5.0: The Return of a Ransomware Leader
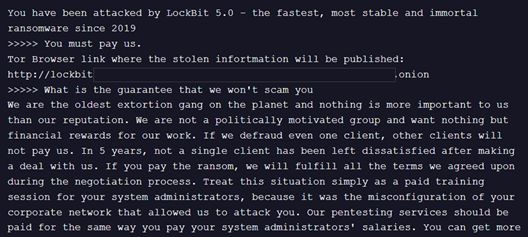
Once thought dismantled, LockBit has re-emerged with LockBit 5.0, an upgraded version featuring multi-platform support (Windows, Linux, ESXi), stronger encryption, and enhanced evasion. LockBit’s return, led by its notorious administrator “LockBitSupp,” signals a possible re-centralization of affiliates seeking stable, reputable RaaS brands.
Notable Details
- Over 15 confirmed victims have already been attributed to LockBit 5.0.
- Affiliates are required to pay a $500 deposit to join, indicating a vetting effort.
Qilin Leads 2025: Profit Over Ideology
Qilin has emerged as the most active ransomware group of 2025, averaging 75 victims per month in Q3, doubling its activity from early in the year.
Though the group claims ideological motives, Check Point Research finds its campaigns to be purely profit-driven, targeting a broad range of sectors and regions.
- Responsible for 30 attacks in South Korea’s financial sector between August and September.
- Offers affiliates up to 85% revenue share, making it one of the most attractive RaaS programs.
DragonForce: Marketing Meets Malware
Emerging actor DragonForce is redefining how ransomware groups compete, not through code but through branding. By announcing “coalitions” with LockBit and Qilin on underground forums and offering “data audit services” that help affiliates identify high-value files, DragonForce blurs the line between extortion and analytics.
- 56 victims were listed in Q3 2025.
- Focused on Germany and high-revenue companies.
- Promotes itself with aggressive PR and recruitment on criminal forums.
This self-marketing trend illustrates how criminal RaaS operators now compete like startups, differentiating through features, brand visibility, and affiliate incentives.
Geographic and Industry Impact
Top Targeted Regions
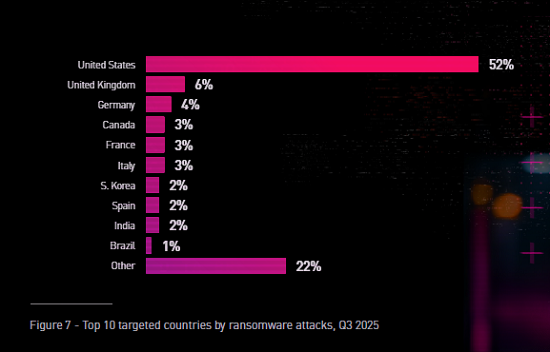
- United States: approximately 50% of global ransomware victims.
- South Korea: entered the top 10 for the first time due to Qilin’s financial campaign.
- Germany, United Kingdom, and Canada: remained major targets for groups such as INC Ransom, Safepay, and DragonForce.
Most Targeted Industries
- Manufacturing and business services, each representing about 10% of attacks.
- Healthcare, stable at 8%, though some major RaaS brands often avoid these targets to limit scrutiny.
The Bigger Picture: Law Enforcement Takedowns vs. Affiliate Adaptation
Despite numerous takedowns, overall ransomware volume remains stable at 520 to 540 victims per month.
Why it happens?
- Law enforcement primarily targets infrastructure and core groups, and not affiliates.
- Affiliates migrate quickly or form new groups after disruptions.
- The result is short-term dips and brands disappearance but long-term resilience in overall attack volume.
Outlook for Late 2025 and Beyond
The re-emergence of LockBit, combined with the fragmentation of smaller groups, points toward a hybrid future: decentralized but orbiting powerful legacy brands.
Check Point Research expects:
- Continued affiliate-driven operations across smaller leak sites.
- Rising monetization strategies such as “data audits” and multi-extortion models.
- Persistent targeting of sectors with high ransom potential.
“In Q3 2025, ransomware proved that disruption doesn’t mean decline,” said Sergey Shykevich, Threat Intelligence Group Manager at Check Point Software. “We’re seeing a highly adaptive ecosystem where affiliates move freely between brands, new actors emerge weekly, and data-first extortion continues to dominate the playbook. The future of ransomware lies in automation, intelligence sharing, and agility — and so must defenders’ strategies.”
Conclusion
Ransomware remains the most adaptive and profitable form of cyber crime in 2025. The balance between fragmentation and re-centralization will define the threat landscape for years to come.
Organizations must continue to:
- Strengthen endpoint and network defenses.
- Maintain offline, immutable backups.
- Educate employees against phishing and credential theft.
- Monitor for emerging RaaS infrastructure and affiliate activity.
Please find the link to access the detailed report for your reference.