Historical data helps Internet of Things resist hacks
The power of big data is used in a strategy developed by A*STAR to improve the security of networks of internet-connected objects, known as...
The biggest cybersecurity threat facing federal agencies is legacy IT
Improving our cyber posture is among the top priorities for the Trump administration. However, there are still many questions raised as to how they...
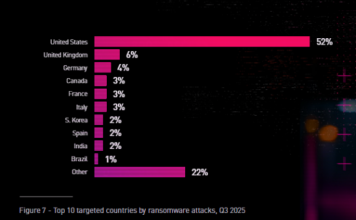
Cyberattacks on govt sector doubled in 2016: NTT Global Threat Intelligence Report
The number of cyberattacks on the government sector globally doubled to 14% in 2016 as per the latest edition of Executive’s Guide to the...
Cybersecurity Pros Will Soon Patrol Computer Networks Like Agents in ‘The Matrix’
Security analysts could soon become the first employees asked to show up to work inside virtual reality.
Thanks to a new virtual reality tool built...
Security & Counter Terror Expo: Integrating cyber and physical security
The high wall between physical and cyber-security was a recurring theme at this year's Security and Counter Terror Expo at London's Olympia centre provided...
Major Defense Company to Adopt Blockchain Cyber Security Tech
The security and aerospace company Lockheed Martin has contracted Guardtime Federal to provide blockchain cyber security. Guardtime Federal will be a key supplier to...
Social media emerging as the most valuable target zones for cyber attackers
Next time you post details about your workplace and job description on social media websites, be careful you could emerge as the potential target...
DARPA and Advancing Cybersecurity Infrastructure With Blockchain
Cybersecurity infrastructure is taking a leap forward with the support of the Defense Advanced Research Projects Agency (DARPA), the research unit of the U.S....
8 Considerations in Cybersecurity Risk Management
Cybersecurity risk management boils down to three key factors:
The probability of an event occurring;
The severity of impact if that event occurs; and
...
Cybersecurity Has a Serious Talent Shortage. Here’s How to Fix It
It’s a refrain I’ve been hearing for the past 18 months from clients all over the world: “We need more skilled people for our...