“You clicked on an infected message…” In my prior life of managing an enterprise email environment, I started thousands of messages with that response to the victims of the infamous “love bug” email.
Looking back, this was a simple task compared to what we now face. Over the past 20 years, I have been on the front lines of the cybersecurity battlefield and fortunate to serve among some of the greatest professionals in our industry. During this time, I have witnessed the landscape shift from annoying hacker hobbyists to the advanced tactics of nation-states and well-funded organized cyber-criminals. The evolution of attacks is advancing at a record pace, and we are at full throttle inside a digital transformation, I don’t suspect any slowing of the pace of innovation coming from threat actors. In fact, trends indicate the opposite. We have the rise of cyber-terrorists, improving anti-forensics approaches, and non-malware approaches to attacks using in-memory, PowerShell-based, and WMI-based, to name a few.
“How do we stop these new threat actors?” is a common question I am asked. Unfortunately, the landscape is far too complex for a simple answer, and the more appropriate question is “How can we maximize the cost of an attack, for the attackers, so these threat actors leave us alone?” Similarly, if your home is more difficult to rob than your neighbor, you become a much less attractive target. Therefore, how can we increase our security posture in a world where the “identity” is the new network edge, all the while that identity works in coffee shops, airports and wifi hotspots around the globe? If your security posture relies on a human firewall to determine if a website or document is malicious, then you may be the most desirable house in the neighborhood for criminals.
In my years of leading operational teams and working among many of the greatest minds and enterprises, I have picked up keen insights that can improve security hygiene and increase the difficulty for any attacker. Before we dive in, state one truth loud and clear: “I am already breached”. This doesn’t necessarily translate to you being under a hostile attack, but the “assume breach” posture sets a very important tone, and unfortunately is likely to be your reality.
 In Asia, we especially find enterprise security is commonly based on firewalls and legacy antivirus technologies. Given this reality, we find that an overwhelming, and I mean OVERWHELMING, majority of endpoints have evidence of malicious artifacts, i.e. they have already been breached.
In Asia, we especially find enterprise security is commonly based on firewalls and legacy antivirus technologies. Given this reality, we find that an overwhelming, and I mean OVERWHELMING, majority of endpoints have evidence of malicious artifacts, i.e. they have already been breached.
According to a recent FireEye report, we find that a majority of attacks in Asia go undetected for as many as 520 days and 55% of the time are detected by external entities, not by our firewalls and antivirus technologies! Our numbers in Asia are improving, as well as globally, but not fast enough.
Now that we have assumed breach, how can we increase the cost of an attack? Here are 5 essentials that I have witnessed make a difference:
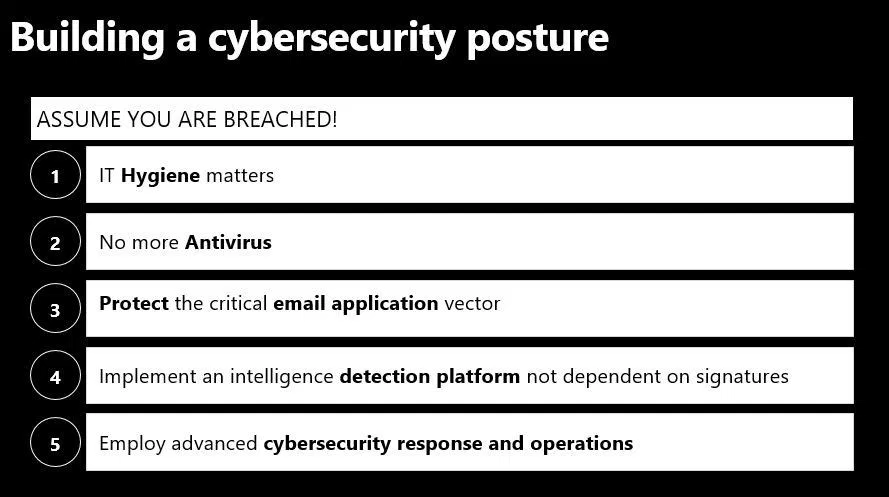 1. Hygiene matters. Remember our parents always saying, “wash your hands”? Turns out they were right! Same is true in technology. Here are the minimum operating guidelines and the operational security equivalent to washing your hands:
1. Hygiene matters. Remember our parents always saying, “wash your hands”? Turns out they were right! Same is true in technology. Here are the minimum operating guidelines and the operational security equivalent to washing your hands:
- Know your environment, especially your high value assets
- Patch and install maintenance updates, prioritize your high value assets
- Use complex passwords and encryption
- Implement hardened administration and networks
- Maintain logging
2. Endpoint modernization. Many of us have modernized in a siloed and bolted-on approach. We have signature-based antivirus, some compliance encryption that drives up our helpdesk calls, and for a few, an endpoint detection and response technology. Each of these likely requires agents consuming critical resources and making our end users shout our names unkindly. The siloed approach requires our operations teams to stitch together and inundate an already overworked Security Info & Event Management system, aka SIEM. A modern endpoint fully integrates these functions and leverages virtualization and container technologies for isolation. The essentials of modern endpoint protection are to:
- Perform the basics of anti-virus
- Protect a user’s identity and contain lateral movement
- Contain ransomware encryption
- Leverage an intelligence platform to detect indicators of attack and compromise
- Capture critical information to replay a breach in motion for advanced forensics
3. Email application protection. There is a common saying in the USA that a “bad day fishing is better than a good day at work”. Allow me to iterate with “a bad day of phishing is a great day at work”. According to the Verizon Data Breach Investigations Report, 77% of modern attacks start with an email where it is too easy to find patient zero. I am surprised by enterprises that continue to implement hygiene services for anti-spam and anti-virus but don’t employ sandboxing or URL rewrite capabilities. Unless we want the human firewall to continue to be our last line of defense, email is a critical application to secure. Vital features are:
- Anti-Spam/Anti-Virus
- Sandbox detonation of attachments
- URL re-write
4. Intelligence platform. Today’s modern attacks are based on unknowns. This is why signature based technologies like antivirus are not succeeding. Intelligence must be based on a vast data set that can model indicators of attack and indicators of compromise quickly, then deliver these through technology. Enterprises that have developed this platform are at a distinct advantage to better hunt and detect the unknown behaviors that may result in an attack.
5. Cybersecurity response and operations. People remain a critical component to success. There is no ignoring the shortage of professionals in security, and the demand continues to grow. According to Michael Brown, CEO of Symantec, to help defend us in this new space, “The demand for the (cybersecurity) workforce is expected to rise to 6 million (globally) by 2019.…” In a recent post, Ann Johnson, VP of the Enterprise Cybersecurity Group at Microsoft, championed an important best practice and case for change to help us address this shortage. Ensuring readiness, training and advanced operations are in place is critical. I am never surprised with the silence I often receive when I ask: “What is your first step in your cyberbreach response plan when you have detected a breach?” This needs to be a top priority of any CISO and CIO.
Microsoft recently published a reference guide to address incident response. The response plan must include the technology team, executives, legal, marketing, risk and other relevant business stakeholders. Too many times these plans include only the technology teams. Next, enterprises must reduce the noise of alerts and ensure that their detection efficacy is feeding them the alerts that matter. The operations teams must move from reactive alert management to proactive hunting by sweeping endpoints and environments for malicious behavior and artifacts.
The latest innovation in threats is non-malware attacks – where threat actors leverage system processes like WMI and Powershell to fly beneath the radar. Identifying these abnormalities with managed sweeps is a new critical operational process. Additionally, the operations teams must consistently run red team/blue team drills to refine their skills and identify potential weak points. Furthermore, adopt an Incident Command System (ICS) for Crisis Management and include executives, legal, marketing, finance, risk and other critical business functions in the incident response plans. Enterprises who have adopted these tactics are at a distinct advantage.
The positives of digital transformation far outweigh the risks and changing threat landscape. We must all assume we have been breached and transform our people, technology and processes to decrease the time it takes to detect a compromise and remediate. Making it more expensive for a threat actor is the biggest deterrence and the steps above significantly increase the hacker cost per comprise.
This post is authored by Michael Montoya, Executive Advisor, Enterprise Cybersecurity Group Asia Region.
Source: https://blogs.microsoft.com

















