Embedded systems are the driving force for technological development in many domains such as automation products, industrial monitoring, control systems, automotive and many more. As the number of connected devices continue to grow, this in turn has also led to tremendous cyberattacks worldwide.
Attacks could be focused on obtaining data for later use, or on compromising the functionality of a system to inflict damage directly. Each type of attack will focus on different components of the overall system. These attacks can damage our infrastructure, systems, and way of life. One of the major issues in IoT security is the lack of security in the IoT devices themselves.
The challenges in embedded system security:
- Unauthorized software execution
Software running on the device can be easily attacked by the hackers where they can modify the software and cause security breach. Cryptographically signed code along with hardware support to verify code is authenticated to ensures software has not been tampered.
- Data security
Privacy of data is the main concern when all devices are connected to internet and are prone to remote attacks. Data security ensure data confidentiality though encrypted data storage and/or encrypted communication.
- Protect against cyber attacks
Connected devices are vulnerable to attacks, the first requirement you might think of is to have a secured method of communicating with devices. Proper authentication is needed to ensure that only authorized personnel can log in.
- Unauthorized device production
The best way to overcome unauthorized device production is to include security into the hardware, which ensures that the device is running authentic code. Hence device manufacturers need to ensure that devices are designed with security in mind, not just consider security as an afterthought.
- Secure software updates (OTA)
A method of secure code updates ensures that the code on the device can be updated for security patches. Use of signed code (secure boot) ensures that malicious code cannot be introduced into the system.
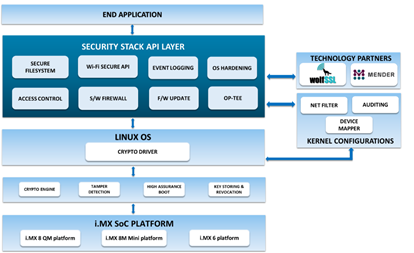
iWave Security Suite Architecture:
Security suite secures connected devices, enabling them with security functions such as encryption, storage, data transmission, and certificate management. The easy-to-integrate solution helps address the security challenges creating a safe and secure environment. iWave’s security suite provides end-to-end security and prevents the information/data in the system from being hacked. Security Suite includes secure boot, Wi-Fi secure API, event logging, OS hardening, access control, software firewall, and secure firmware update to name a few
Security Suite development kit:
iWave offers Security Suite development kit, which is developed for different variants of NXP i.MX 8 and i.MX 6 high-performance applications processors. The development kit includes a software kit to help customers learn about and quickly implement Security Suite into their products.
Supported hardware development platforms:
- i.MX 8 QM/QP SMARC development kit
- i.MX 8M Mini SODIMM development kit
- i.MX 6 UL/ULL SODIMM development kit
Following are the Security Suite packages:
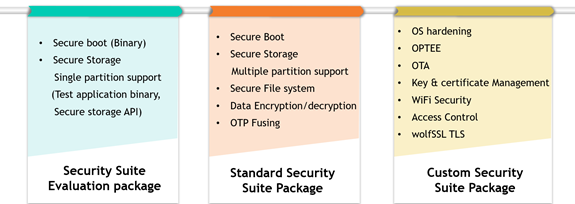
Getting started with Evaluation package:
This package allows customer to evaluate the secure boot and secure storage features in i.MX 8M Mini and i.MX 8 QM platforms.
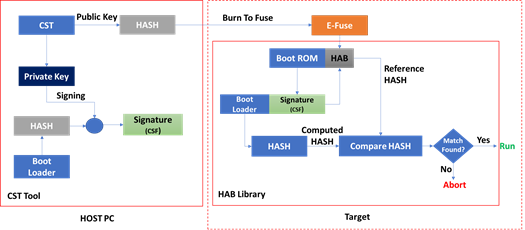
- Secure Boot
- Protect against:
- Attackers with a physical presence to the device modify code stored in cold storage
- Attackers with code execution (i.e., malware) to create persistence
- Provides:
- Authentication (unauthorized images not allowed to run)
- Integrity (authorized images cannot be ‘tampered’ with)
- IP protection
- Uses asymmetric key for signing
- Private key is used for signing
- Public key is used to verify signature
There is lot more precautions to be taken care when fusing the keys to the board and signing the binaries. iWave offers OTP fusing API and Signing Tool which do the work in just one step.
- Secure Storage
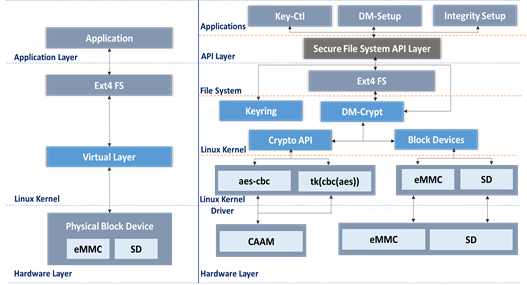
- Persistent data store for crypto keys or other application-specific data
- Secure file system using device mapper kernel framework.
- Device mapper works by passing data from a virtual block device to another block device. With this approach, physical block will not be accessible to user space.
- All read/write will happen using encrypted and integrity enabled virtual block.
- When user writes the data to the virtual device, every block of data is encrypted and stored on the physical device.
- When user reads from the virtual device, every block is decrypted at run-time.
- Because of this feature, once encrypted partition is unlocked and mounted, User will be able to use encrypted partition like normal partition.
- In Linux kernel, dm-crypt and dm-integrity configuration is used to enable virtual encrypted block with integrity support. Configuration of the device mapper is performed using the dmsetup utility.
iWave offers secure storage API and Data encryption decryption API to encrypt the block of storage or the piece of sensitive information.
With an attacker having enough time, resources and motivation to always break into any system, there is no guarantee for security. For this reason, iWave provides Security Solution to products to protect against specific threats trying to achieve a balance between the cost of security implementation and the benefits obtained. More information on the Security Suite can be found here or a quick 1-minute video can be viewed here


















