Cognitive Defence: How Mindfulness Can Help Thwart Cyberattacks
Up to 90% of all successful cybersecurity attacks involve social engineering; exploiting human vulnerabilities. While technical measures like strong passwords and anti-virus...
WotNot exposes 346K sensitive customer files
Introducing additional hands into the AI supply chain might not be such a great idea. Passports, detailed medical records, resumes, and other...
Learn how to navigate the Cyber Resilience Act (CRA) with free online live training...
Direct Insight, the UK-based technical systems integrator & reseller of system-on-module (SoM) & other embedded systems, will host a live online training...
NordLayer integrates malware detection feature from NordVPN to elevate business security
The most common file formats for hiding malware are .exe and .zip, according to research by NordVPN. These are also the file...
The Cost of Cyber Attacks for Manufacturing Businesses
As IT and the internet continue to change, manufacturing businesses are increasingly vulnerable to cyber attacks. Historically, the manufacturing sector focused on...
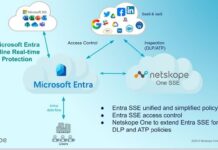
Netskope partners with Microsoft to offer enterprise customers advanced SSE capabilities
Netskope, a leader in Secure Access Service Edge (SASE), announced the extension of its partnership with Microsoft to provide advanced Security Service...
India’s Malware Risk Ranks 26th in October: Formbook Dominates as Top Threat, Healthcare Sector...
Check Point Software Technologies Ltd., a leading cyber security platform provider of AI-powered, cloud delivered solutions, has released its Global Threat Index...
GMV secures major contract for ESA’s CyberCUBE mission to bolster Space Cybersecurity
Highlights:
The CyberCUBE mission is a bold step forward in ESA’s efforts to safeguard its space infrastructure
Netskope further extends data security with new DSPM capabilities
Netskope, a leader in secure access service edge (SASE) and security service edge (SSE), announced new enhancements to the Netskope One platform,...
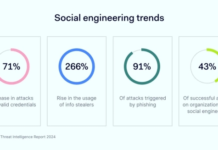
9 out of 10 cyberattacks happen because of human vulnerability
Social engineering attacks pose a significant threat to businesses and individuals alike. They manipulate emotions instead of targeting technical vulnerabilities. These sophisticated...