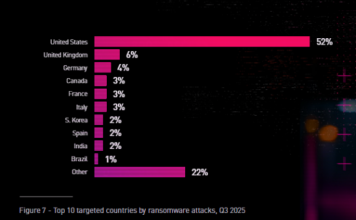
Cyber security lab coming up in Tirupati
A world-class cyber security lab with the latest gadgets to carry out investigations and advanced research facilities is being established in Tirupati by the...
Cyber security for automation
IT security services
Cyber security is becoming an increasingly important issue in process automation and particularly for process control engineering. As networking in process automation...
New DARPA program seeks cybersecurity through hardware design
Pentagon scientists say they could stop 40 percent of current cyberattacks by producing secure computer chips, and Friday they explain how to a closed-door...
Check Point Introduces the Cyber Security Architecture of the Future: Check Point Infinity
Check Point Software Technologies Ltd. (NASDAQ: CHKP) today introduced Check Point Infinity, a revolutionary cyber security architecture designed to meet the critical security needs of...
Strategies to build your cybersecurity posture
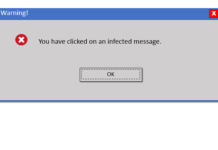
“You clicked on an infected message…” In my prior life of managing an enterprise email environment, I started thousands of messages with that response...
Argus Cyber Security Hacks Car Using Dongle Device
Argus Cyber Security, the Israeli cybersecurity company, said late last week that it was able to hack into a vehicle’s internal communication system using...
‘Web cops’ to check cyber crimes in Andhra Pradesh
HYDERABAD: With cases of cyber security breaches increasing by the day, Andhra Pradesh has decided to introduce the concept of 'web constabulary'. In fact,...
How AIG’s Cyber Security Gamble Could Pay Off
American International Group (AIG) has recently begun offering personal cyber security insurance plans to individuals. The company appears to be riding a wave of...
What is BrickerBot?
It was only a matter of time until a new type of malware would target Internet of Things devices. BrickerBot, as this new threat...
These Are 10 Cybersecurity Myths That Must Be Busted
Cybersecurity was huge in 2016. From ransomware to weaponized Internet of Things (IoT) devices to foreign hacking of elections – last year saw it...