
Social Engineering: One of the world’s most famous hacker Kevin Mitnick explained in his book “The Art of Deception” the power of social engineering techniques and today we all know that social engineering can be used to power cyber attacks. Pretexting is the most common technique of social engineering based cyber attacks in which criminal present oneself, someone else just by creating fake identity. In this case criminal get as much as information about victims and launch the attack based on the information collected by social engineering.
Password Guessing: Password guessing is very basic technique also known as brute force attack, a people often faces while developing their web based solution. A brute-force attack is an attempt to discover password by making thousands of possible combination of letters, number and symbols to find the correct password. Kali Linux is worldwide used tools for password guessing. Actually it was designed for penetration testing but people started it for cracking the passwords of other’s password protected WiFi network.
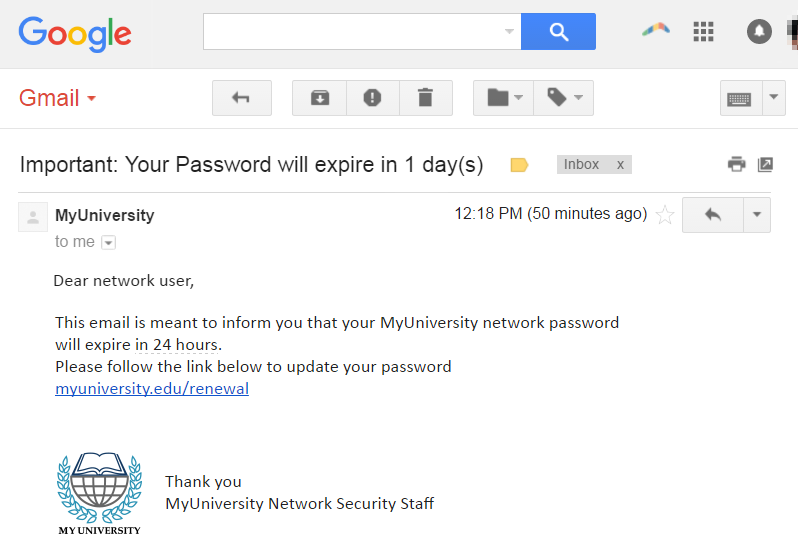
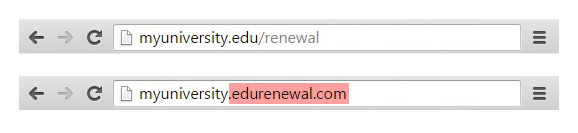
Phishing: Phishing is one of the most common and deadliest attacks in cyber world. It’s an attempt to obtain sensitive information such as username, passwords and credit card detail. Phishing is typically carried out by email spoofing or instant messaging and direct users to the fake websites which looks and feels like real one and the only difference is URL. The world’s most famous Ransomware attack was done by Phishing technique only in which a download link downloaded the virus on victim’s computer and encrypted the whole system.
Below is the example of a phishing attack.
KeyLogger: Keylogger is another common hacking technique, hackers often use to gather sensitive information of a victim. Keylogging or Keyboard capturing, is the action of recording the keys struck on the keyboard and the person using the keyboard is unaware that their action is being monitored. A Keylogger can be either software or hardware.
Waterhole Attack: Watering hole is a computer attack strategy, in which the victim is a particular group (organization, industry, or region). In this attack, the attacker guesses or observes which websites the group often uses and infects one or more of them with malware.
Fake WAP: This is one of the most common hacking technique hackers use to gather sensitive information from victims computer or mobile devices. In this method hackers create a fake WiFi Network which looks like a genuine public place WAP. Once you get connected to the fake WAP, a hacker can have access to your device data. This is the easiest hacking method where you just need a simple software and WiFi network. And its easy to name your WAP a legitimate name like “Starbucks Wifif” “Railway WiFi” etc.
Virus, Trojan etc: Virus or Trojans are malicious software programs which get installed on victim’s system secretly and send data to the hackers. Once installed on your system, these programs can lock your files, serve fraud advertisement, divert traffic, sniff your data and spread all over the network your computer is connected to.
Click Jacking attack: Click Jacking is also known as UI redressing where a hacker can hide an actual clicking point where a user has to click and can direct a user to the desired webpage. This technique is can be seen on number of free movies and games sites, where a publisher uses this technique to earn from advertisement.
Cookies Theft: High end hackers use this technique to gather victim’s saved user name and passwords on his computer browser. The cookies of a browser keep our personal data such as browsing history, username, and passwords for different sites that we access. Once the hacker gets the access to your cookie, he can even authenticate himself as you on a browser. A popular method to carry out this attack is to encourage a user’s IP packets to pass through attacker’s machine.
Bait and Switch: Most commonly used technique to attract a victim in a trap. Using bait and switch hacking technique, an attacker can buy advertising space on a website to run attractive offers. Once you click on the ad, he might direct you to the desired pages infected with malware. This way a hacker can install malware on your system without your permission and can perform the desired action. Offers are run in a way so a victim ends up clicking the ads.



















