Netskope Advances AI-Ready Data Security with Visibility and Analytics of Data Lineage
Netskope, a leader in modern security and networking for the cloud and AI era, announced Netskope One Data Lineage, providing visibility and...
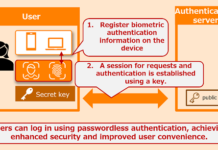
Fujitsu introduces biometric authentication service for SMBC Nikko Securities Online Trading
Fujitsu Limited announced that SMBC Nikko Securities Inc. has adopted Fujitsu's passkey authentication service (FIDO2 standard) for its web services, including online...
Think Before You Scan: That QR Code May Be a Scam
QR code scams:
In quishing attacks, cybercriminals place QR codes containing malicious links in public places, such as...
Why Network Traffic Monitoring Is Mission-Critical in 2026
Network traffic monitoring has evolved from a nice-to-have administrative tool into an essential cybersecurity defense mechanism. As organizations face increasingly sophisticated threats—from...
Introducing Acronis Archival Storage: A Long-Term Data Protection Solution
Acronis Archival Storage:
Acronis, a global leader in cybersecurity and data protection, announced the launch of Acronis Archival Storage, a long-term,...
New Wireless Broadband Alliance Report Helps Enterprises Integrate Private 5G Securely Into Existing IT...
The Wireless Broadband Alliance (WBA), the global industry body dedicated to driving the seamless and interoperable service experience of Wi-Fi across the global wireless...
Generative AI to Fuel Fraud and Impersonation Attacks in 2026, World Economic Forum Warns
Generative AI fraud and impersonation attacks 2026:
Ransomware attacks are no longer the top concern for CEOs; instead,...
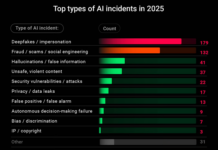
346 AI incidents in 2025 – from deepfakes and fraud to dangerous advice
AI incidents in 2025:
2025 was a big year for AI incidents. According to the AI Incident Database, there...
A quantum leap: Preparing for a new age of computing
We are entering the age of quantum computing. What once belonged to theory is now moving into application. Early models are already demonstrating the disruptive...
Almond launches a Resilience Operation Center (ROC) dedicated to operational cyber resilience
Designed as a concrete response to a new cyber era, Almond's Resilience Operation Center (ROC) embodies a pioneering approach: a unified, continuous...