WinMagic launches SecureDoc Cloud VM Version 8.1
WinMagic, an award-winning encryption and intelligent key management security solution provider, today announced the launch of its latest software release for Cloud, SecureDoc 8.1.
This...
Fujitsu Begins Large-Scale Internal Deployment of Palm Vein Authentication to Accelerate Workstyle Transformation
Fujitsu today announced that this year it will steadily roll out a large-scale deployment of its palm vein authentication technology within the company.
The password-based...
Two-year study explores the roles of information security leaders and how they are affected...
Synopsys, Inc. today published the inaugural CISO Report, the result of a two-year data-driven study exploring the roles of information security leaders and the organizational...
Five-member board of experienced security executives to guide technical innovations of Synopsys security products...
Synopsys, Inc. (Nasdaq: SNPS) today announced the formation of a Technical Advisory Board (TAB) to guide the technical direction of the Synopsys Software Integrity Group's security products and...
Argus Cyber Security and STMicroelectronics Cooperate to Strengthen Security and Privacy of Connected Automotive...
Argus Cyber Security, a global leader in automotive cyber security, and STMicroelectronics, a global semiconductor leader serving customers across the spectrum of electronics applications, announced...
First Biometric EMV card for Contactless Payments by Gemalto
Biometric authentication replaces PIN code facilitating higher value contactless transactions
Maximum privacy protection ensured by secure in-branch enrolment process and on-card storage of...
Indian INCs Look at Investment in Security Big Time in 2018
2017 will undoubtedly be considered as ‘Year of ransomware’, the year when the global security landscape was forever changed by attacks like WannaCry and...
Role of Operating system in Security
Computer system and software design should address the legitimate security concerns and incorporate appropriate safeguards and mechanisms for enforcement of security policies. On the...
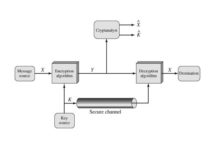
What is the Conventional Encryption Model?
Symmetric encryption is also referred to as conventional encryption or single-key encryption. It was the only type of encryption in use prior to the...
Next-generation Firewall Platform: Sophos XG Firewall v17
Sophos XG Firewall provides unprecedented visibility into your network, users, and applications directly from the all-new control center. At Sophos, we’re all about making...